The well-known threat of domain hijacking has once again resurfaced. This time, however, fraudsters shifted their focus away from sports-related websites and instead targeted higher-trust assets – government and educational subdomains that were vulnerable to this type of attack.
What was uncovered
In February 2025, the Adex team was routinely monitoring advertising campaigns when an unusual anomaly was identified – suspicious patterns appearing exclusively across a narrow set of countries and verticals. At the time, the nature of the underlying threat was unclear, prompting the team to conduct a deeper analysis of these patterns.
This initial finding triggered a broader investigation, during which additional similar cases were collected and reviewed. The analysis revealed that all affected campaigns were directing traffic to landing pages hosted within domain zones reserved for government and municipal authorities, as well as educational institutions in Indonesia, an observation that immediately raised serious concerns.
Such domains are typically owned and operated by governments, municipal authorities, and officially accredited educational institutions. Access to them is granted through formal administrative processes and is limited to authorized organizations only. For this reason, private individuals and commercial advertisers cannot legitimately obtain or use these domains, which makes their appearance in advertising campaigns a major red flag indicating potential misuse or security compromise.
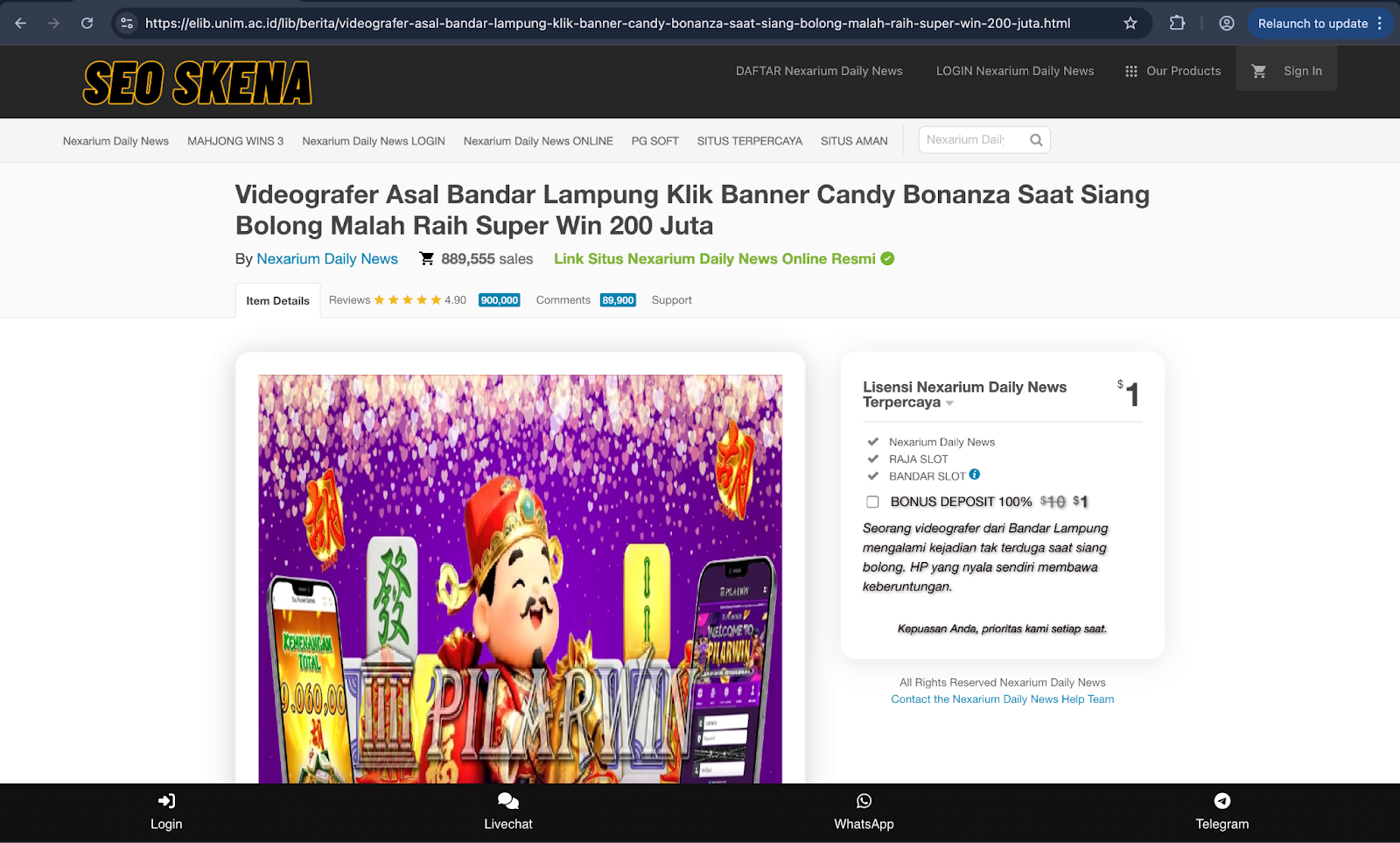
Landing page on the website of Universitas Islam Majapahit
ht**s://elib[.]unim[.]ac[.]id/lib/berita/videografer-asal-bandar-lampung-klik-banner-candy-bonanza-saat-siang-bolong-malah-raih-super-win-200-juta.html
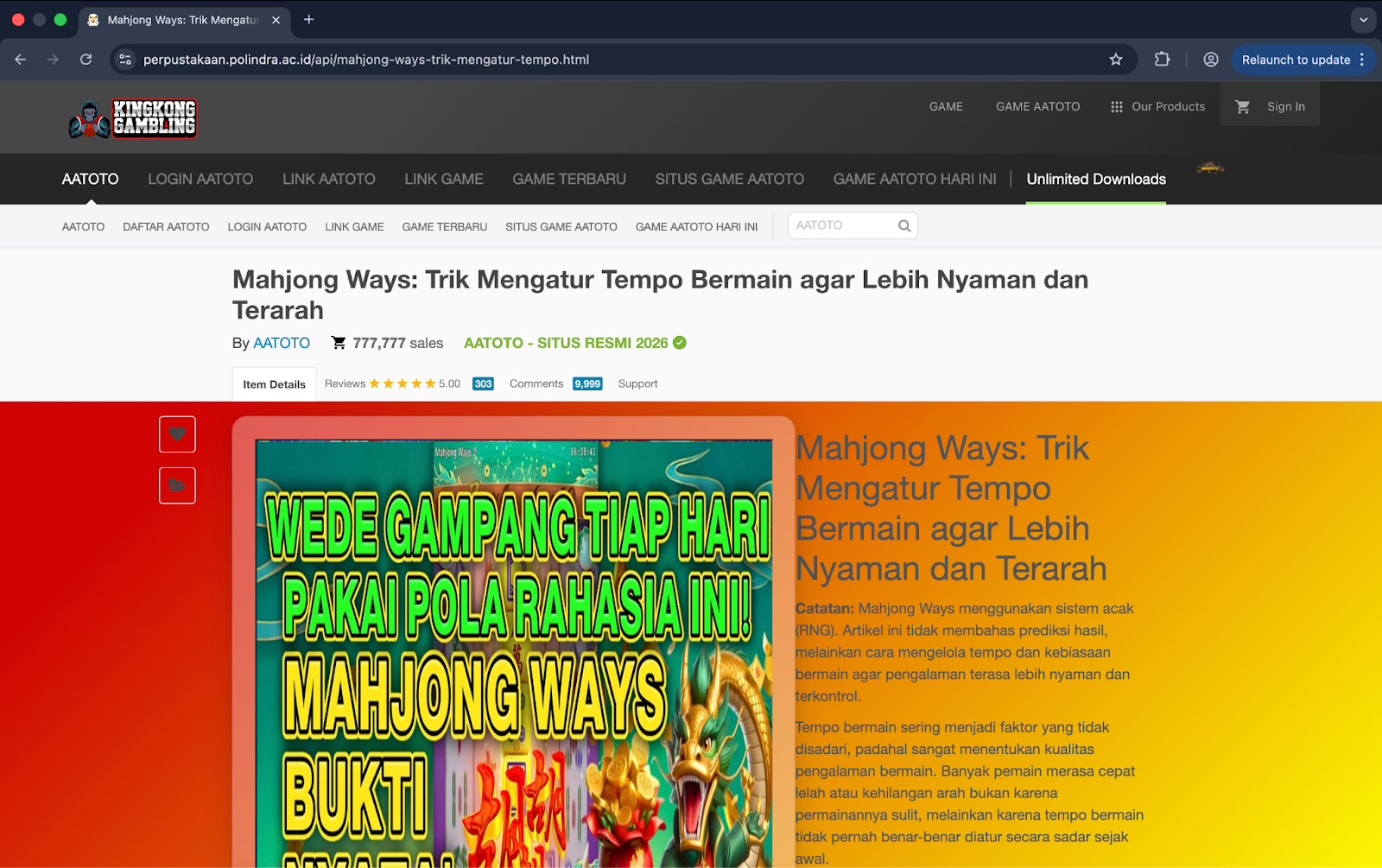
Landing page on the website of Indramayu State Polytechnic h**ps://perpustakaan[.]polindra[.]ac[.]id/api/mahjong-ways-trik-mengatur-tempo.html
Beyond Indonesia, the investigation uncovered similar cases, with landing pages hosted on domains associated with U.S. universities and private companies across other regions.
At this point, the patterns suggested a deeper issue, and the team moved forward with a full-scale review.
Subdomain takeover
It was determined that all landing pages promoted iGaming services, regardless of whether they were hosted on official educational domains or on websites entirely unrelated to iGaming.

Landing page located on the italian groceries website https://crm[.]zarotti[.]it
However, when the team requested further clarification and supporting documentation from advertisers, the information was either not provided or failed to offer any substantive explanation.
As a result of this review, the team had sufficient evidence of unauthorized subdomain usage and was able to take action. To understand how this attack was possible, we looked more closely at the technical setup behind these domains.
According to the OWASP classification, subdomain takeover falls under A05: Security Misconfiguration.
This type of attack occurs when a legitimate domain owner forgets about an existing subdomain and leaves a CNAME record pointing to a cloud storage service.
In our case, it involved third-level domains, as all of the affected websites were structured in this way.
Once the associated cloud bucket is deleted, an attacker can claim the same address and host their own content there, without the knowledge or consent of the domain owner.
In addition to subdomain takeovers, certain cases were also linked to vulnerabilities in web servers or CMS platforms, or to compromised administrator credentials. This suggests that some legitimate domain owners were rather careless when it came to basic security.
Why attackers use domain takeover
Attackers typically rely on subdomain takeover for two main reasons: cost efficiency and increased trust.
By abusing existing subdomains, attackers avoid the need to register new domains and wait for them to build a reputation.
At the same time, content hosted on government or educational subdomains inherits a higher level of trust, allowing malicious landing pages to bypass basic reputation checks and appear more legitimate to users, platforms, and automated filtering systems.
Understanding the motivation helps explain why such attacks remain effective and why a timely response is critical.
How to protect your website from subdomain takeover
The Adex team suggests following a few basic safety practices that would help protect your website from domain takeover:
- Check your subdomains regularly
Remove subdomains you no longer use, especially those linked to external services. - Keep DNS records up to date
Make sure DNS entries do not point to services or cloud resources that no longer exist. - Maintain your hosting and CMS
Update web servers, CMS platforms, and plugins to reduce the risk of known vulnerabilities. - Protect admin access
Use strong passwords, enable two-factor authentication, and limit access to administrative accounts. - Watch for unexpected changes
Monitor your website for unusual content, redirects, or traffic that you did not authorize.
Taking these simple steps helps reduce the risk that your domain will be misused without your knowledge.
Final notes
Ultimately, this case shows that neglected subdomains and weak security practices can quickly turn trusted domains into tools for abuse.
As attackers continue to adapt their methods, maintaining full control over domain infrastructure remains essential: not only to prevent abuse, but also to reduce legal and compliance risks associated with unauthorized domain usage.



