Adex, an anti-fraud platform that helps advertisers detect suspicious events within their traffic immediately, has recently uncovered a new generation of the notorious Triada malware – a threat we’ve been battling since 2020.
Over the past years, this Trojan has grown increasingly aggressive and sophisticated. Today, every major ad network faces its impact, as Triada continuously evolves, deploying new fraud schemes, data-theft techniques, and methods to hijack advertiser accounts and budgets.
Read on to discover how Adex experts and Business Security & Compliance teams of the PropellerAds advertising platform traced and exposed a fraud ring that attempted to use advertiser accounts across major ad networks to distribute Android malware, in some cases through reputable platforms, like GitHub and Discord.
What is Triada and How Attackers Profit From It?
Triada is an Android Trojan first identified in 2016. It began as a modular backdoor and rootkit, granting attackers privileged access and enabling the malware to infiltrate deeply into Android system processes.
What started as an advanced Android backdoor has evolved into a fully fledged mobile cybercrime tool, growing more sophisticated with every new iteration.
Over time, Triada has significantly expanded its capabilities: it can steal sensitive data, hijack communication apps, inject unwanted ads, subscribe users to paid services, and even replace cryptocurrency wallet addresses. Its scale is especially alarming because it targets major apps millions rely on daily – including WhatsApp, Facebook, and Gmail.
According to the latest statistics, in the third quarter of 2025 alone, Triada ranked among the leading mobile threats, accounting for 15.78% of all detected infections.
But how does it reach the device?
Triada spreads through several channels, each designed to maximize reach and monetization. Here are the main methods attackers use:
1. Infection via Modified Apps
A major distribution vector has been modified Android apps such as FMWhatsApp or YoWhatsApp. These unofficial versions were often promoted via paid ads or social media posts, luring users with claims like “enhanced WhatsApp with even more features.”
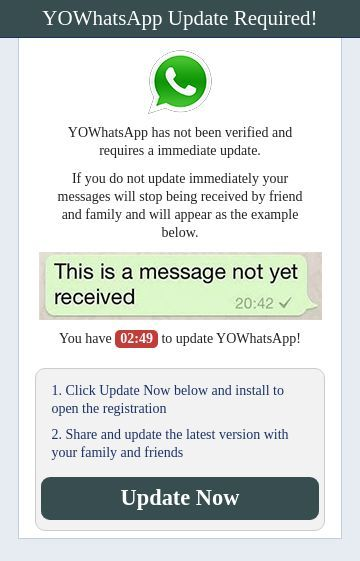
Screenshot from suspended campaign
2. Pre-installation on Counterfeit Devices
In 2025, a massive campaign was uncovered: Triada was preinstalled on counterfeit Android smartphones sold through online marketplaces. These phones were heavily advertised as “cheap, limited-time offer devices”.
When purchased, the Trojan was already present in the firmware, activating on first boot.
Fraudulent Schemes
After the device is infected, Triada can activate one or multiple advertising-related and traffic-manipulation techniques, including:
- Ad redirection & click hijacking: swapping genuine ads with their own placements to generate impressions, clicks, and revenue.
- Forced premium subscriptions: secretly subscribing users to premium SMS or paid content on-demand services, mimicking real ad offers.
- Affiliate fraud: redirecting traffic from real ad networks to fake (fraudulent) ones, faking conversions or views.
- Crypto wallet address replacement: not purely advertising-related, but part of the broader fraud strategy – diverting payments to attacker-controlled wallets.
In other words, Triada is far more than a payment-data stealer – it’s a rapidly evolving, multi-purpose threat with expanding capabilities. That’s why stopping its distribution is critical.
What Adex Has Uncovered
Since 2020, we have been tracking a highly organized threat actor with activity patterns pointing to Turkey that systematically attempted to register advertiser accounts as a delivery vector for this malware.
Latest statistics indicate that Turkey ranks among the top regions targeted by mobile trojans:
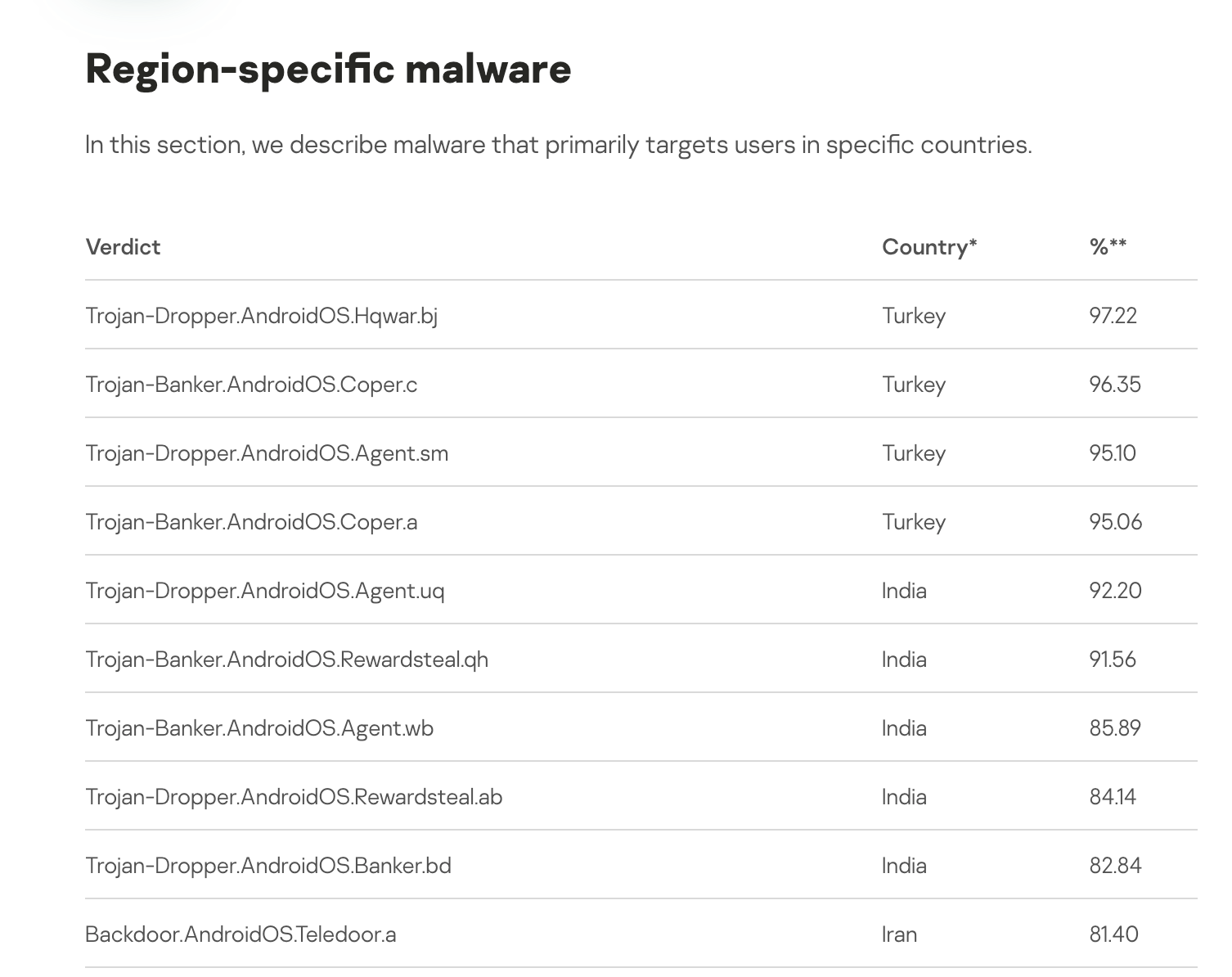
Source: Securelist.com
To date, Adex specialists have identified three major waves of Triada-related attacks and permanently banned more than 500 compromised advertiser accounts.
Over the years, the malware itself has evolved dramatically. Since 2020, we’ve seen it cycle through a series of distribution tactics, including slipping into seemingly ordinary software, experimenting with new delivery channels, attempting to buy ad traffic, and directing users toward its infected sources.
The actors behind it probed for weaknesses in our automated defenses, trying to understand how our detection patterns worked. But throughout this cat-and-mouse chase, moderators kept a close watch, shutting down each new attempt as it surfaced. In many ways, the confrontation has resembled a long, high-stakes boxing match – tense, technical, and relentless, but so far, every round has gone our way. Now we’re ready to walk through these rounds one by one and show how the fight unfolded.
Round 1 (2020-2021)
Our first hands-on encounter with Triada occurred in August 2020, when the Adex team detected unusual activity among a cluster of PropellerAds advertisers presenting themselves as being from Turkey.
Following the initial investigation, it became clear that the advertisers had attempted to pass the KYC procedure with documents that appeared authentic at first glance but were in fact crude forgeries, the kind of falsifications that fail even basic verification checks.
When these advertisers tried to fund their accounts, our systems immediately flagged the payment attempts as matching known carding patterns, triggering an automatic block. The actors persisted, repeatedly attempting to complete payments with different compromised card details, but the safeguards held: every transaction was stopped in time, and not a single cent was lost from legitimate cardholders. Manual verification and further inquiries only confirmed our assumptions, and the campaign launch was denied.
At the campaign settings, the attackers relied on landing pages disguised as “Turkish government citizen support” portals (vatandasdestek – literally “citizen support”). Local Turkish URL shorteners redirected users to apkuploads.com, which then triggered the automatic download of a file named googleplay.apk – the Triada payload.

Screenshot from suspended campaign
In parallel, additional dropper channels were used, including the Discord CDN (cdn.discordapp.com/attachments/…/googleplay.apk) and the kisa.link shortener.
Here are some of the accounts identified as fraudulent:
| GEO | IP | |
| kurtu**us1**5@gmail.com | TR | 188.57.1*5.2*9 |
| t**nguney@gmail.com | TR | 5.*4.1*9.1 |
| do***binboy**@gmail.com | TR | 37.1*4.2*9.12 |
| ***azanekiz1**@outlook.com | TR | 37.1*4.*50.77 |
| **anglin***@gmail.com | ME | 62.4.*5.*25 |
| a***tkent*7@gmail.com | TR | 46.1*5.147.1*9 |
| ***ufkazan9**@gmail.com | TR | 178.2*4.79.1*1 |
| i***s32***2@outlook.com | TR | 85.1*3.203.1*2 |
| s***eaki*@gmail.com | TR | 5.2*.42.1*0 |
Fighting fraud requires constant adaptation, staying one step ahead, and a willingness to learn from every encounter. After studying the behavior of the attackers and the signals they left behind, the Adex team recommended tightening identity checks to stop any future attempts involving forged documents. Acting on these insights, PropellerAds partnered with Sumsub, a leading identity verification provider, to build a more resilient KYC process capable of filtering out even the most convincing fake IDs.
At the same time, the platform enhanced its payment-screening sensitivity, ensuring that suspicious carding patterns are detected and blocked long before any damage can occur. This upgrade further enhanced the network’s ability to detect fraudulent identities early, protect advertiser accounts, and ensure a safer, more trustworthy ecosystem for all.
We held our ground during the first round.
Round 2 (2022-2024)
The second wave marked a clear shift in the attackers’ tactics. Instead of trying to slip past KYC with questionable documents or triggering payment blocks with suspicious top-up attempts, they switched to a far more calculated approach: compromising long-standing, fully verified advertiser accounts. Once inside these genuine accounts, the attackers attempted to repurpose them as a delivery channel for malware, routing traffic through their own domains and cloaking setups.
This new generation of Triada activity was confirmed only after a long-time verified advertiser noticed that one of his campaigns had been blocked and reached out to us for clarification. He had lost access to his account, and our investigation revealed that attackers had taken control and attempted to run suspicious ads using his credentials.
Upon further investigation, it became clear that the advertiser had been reusing the same password across multiple services and had not enabled two-factor authentication. When his email appeared in data leaks and was subsequently hijacked, fraudsters had little difficulty gaining access to his advertiser account.
Our automated system immediately flagged an anomaly: the advertiser typically logged in from France, yet a simultaneous login from Turkey was detected – a clear deviation from his normal behavior.
Using the compromised account, the attackers tried to create several campaigns targeting Turkey, each containing cloaked redirect chains.
The attackers used a cloaking setup targeting Turkey, where the target URL (tasartasartasarla.com) served only as the first step in a multi-layer redirect chain.
After the click, users were forwarded to GitHub, and then to raw.githubusercontent.com, where the actual malicious payload or loader script was hosted.
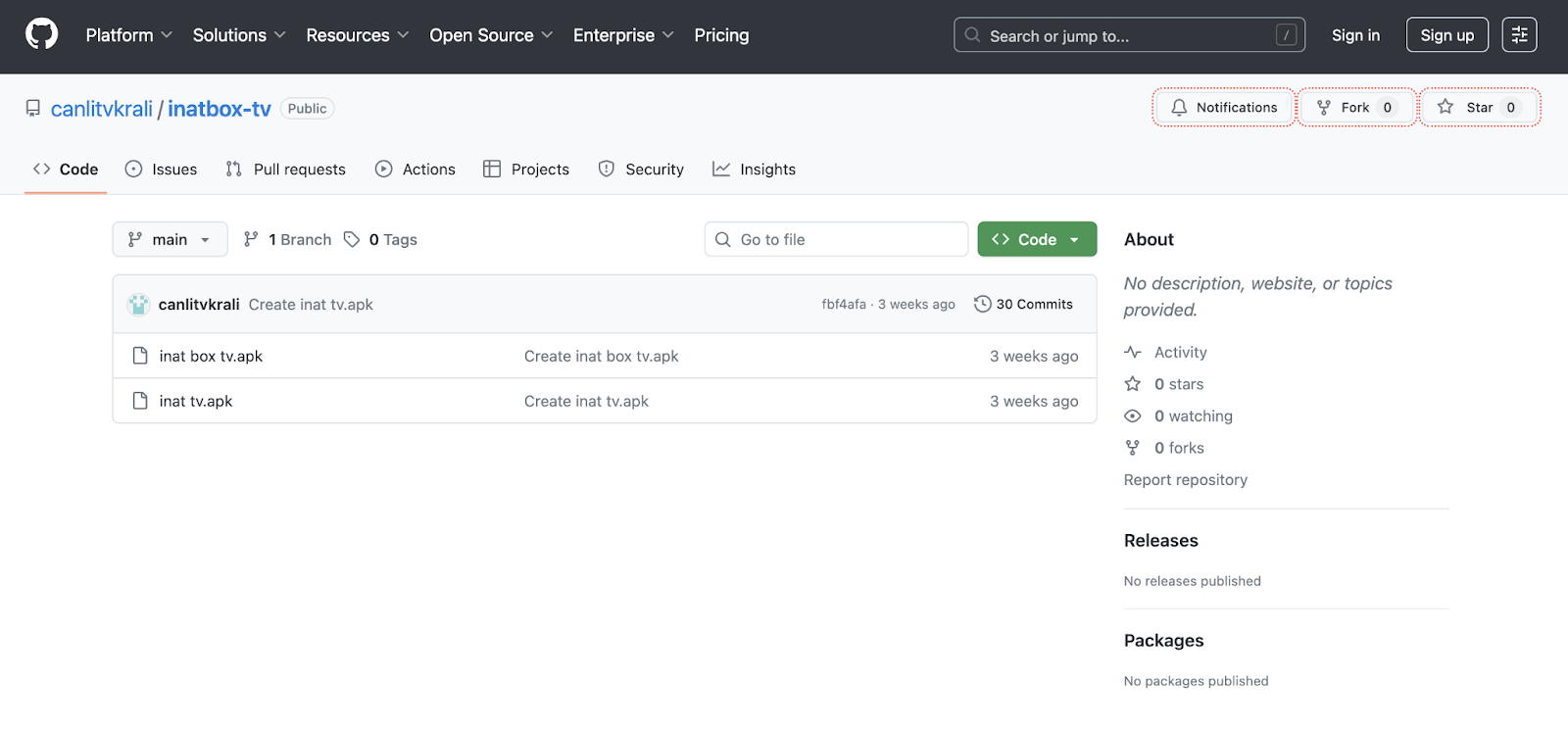
One of the fraudulent APKs is still available on GitHub. We have submitted an official request to GitHub regarding this malware.
This technique allowed fraudsters to hide the real destination behind high-trust domains (GitHub and its CDN), passing moderation and security checks in various advertising networks. It also aligned with other Triada campaigns, where GitHub, Discord CDN, and local shorteners were used as “clean” intermediaries to mask the delivery of the APK.
To ensure that client accounts remain protected – even when some advertisers are careless with their passwords – PropellerAds has implemented, by default, two-factor authentication for all advertiser accounts, with verification via both SMS and email.
We claimed another round.
Round 3 (2025 – Now)
The latest iteration of Triada has already emerged: attackers now use phishing pre-landers disguised as Chrome browser updates, while the malicious files themselves are hosted on GitHub.
Here’s a typical example of such a pre-lander:
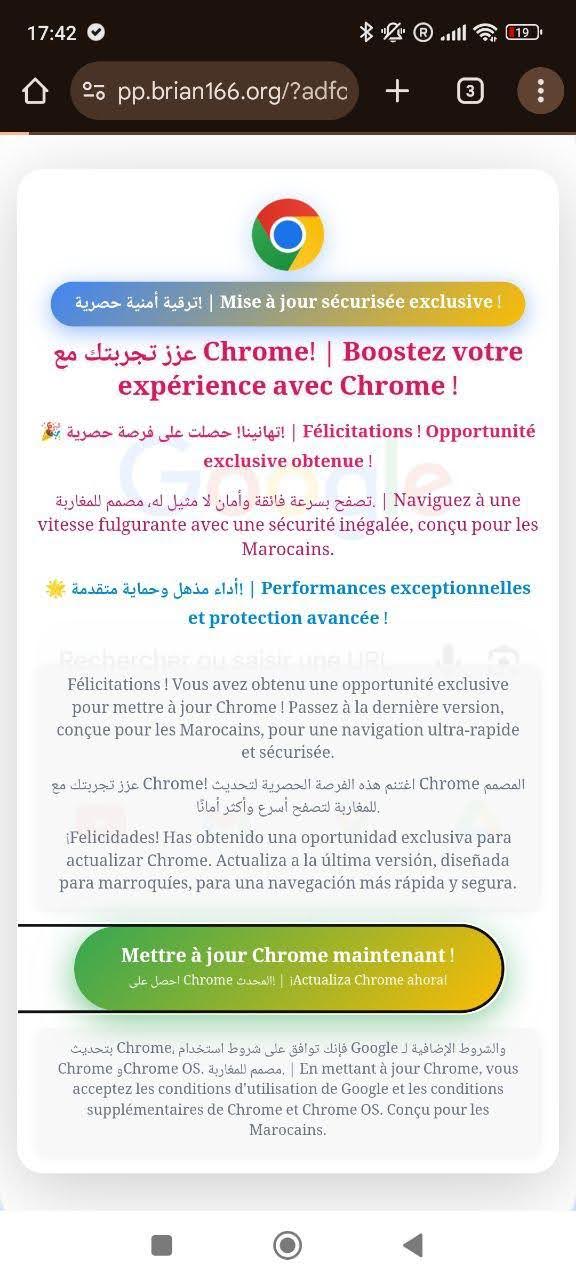
Screenshot from suspended campaign
During the analysis, we identified that the attackers were not relying solely on Triada. They also distributed other banking stealers using similar cloaking chains but with different initial domains, for example, loreastrock.com.
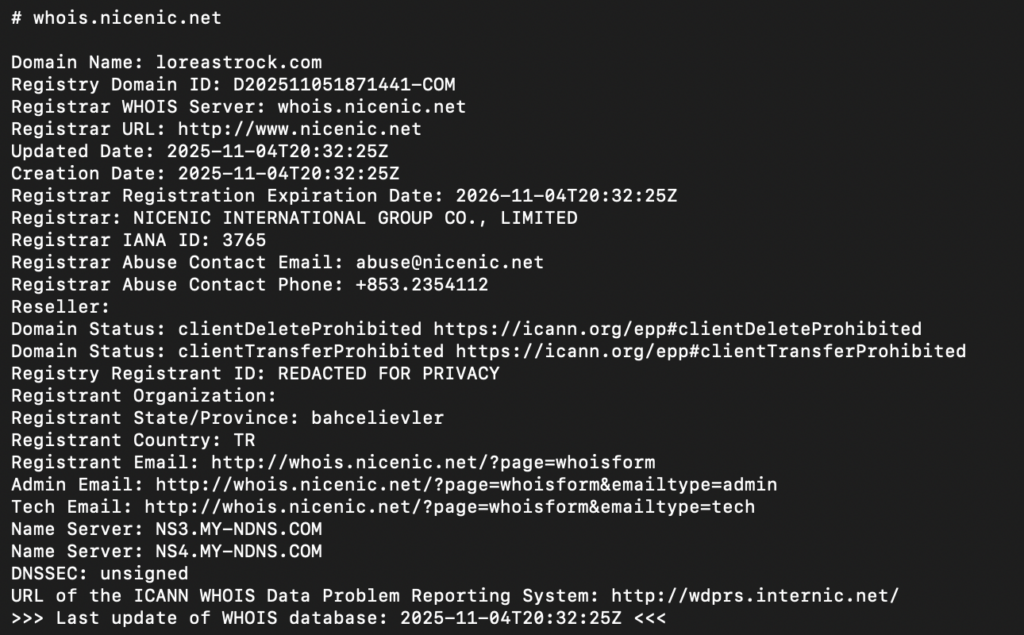
The VirusTotal data linked to these campaigns also revealed multiple hijacked accounts with suspicious logins originating from Turkey and India. This confirmed that attackers were actively taking over long-standing, fully verified advertiser accounts to distribute malicious redirects.
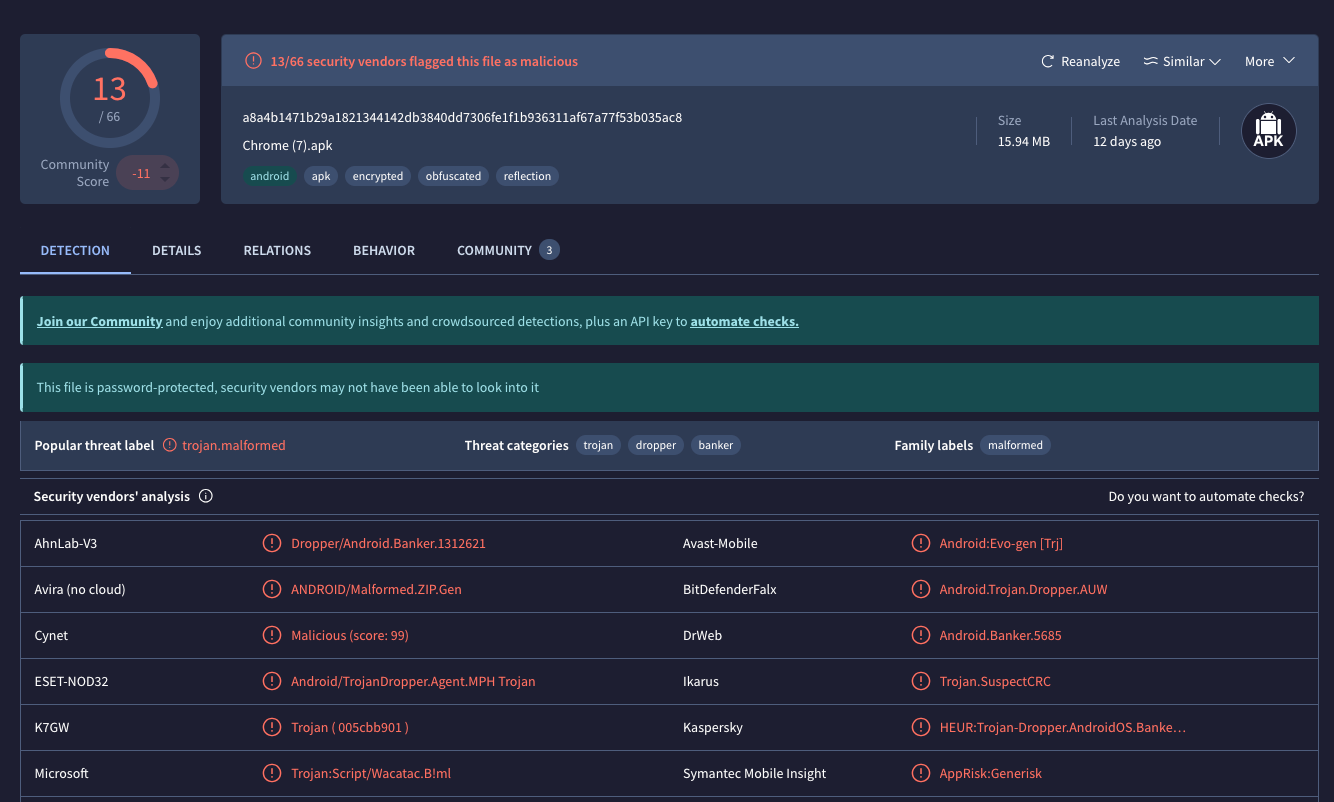
Source: Virus Total
Here are some of the identified accounts:
| GEO | IP | |
| qi***jami**@gmail.com | TRIN | 5.1*7.1*4.221 139.1*7.170.*22 |
| ***rhat9*0@gmail.com | TR | 46.*06.19.*8 88.*44.2*5.230 78.1*0.1*2.20 |
| xli*48**@gmail.com | TR | 46.2*1.2**.22 46.2*1.1*3.20 |
Fraudsters increasingly use reputable platforms like GitHub or Discord to host payloads or disguise malicious redirects, meaning a “clean” domain is not a guarantee of clean intent. As a result, Adex specialists designed a tailored solution capable of thoroughly analyzing each campaign for potential threats.
Today, every campaign passing through PropellerAds, even those pointing to well-known, trusted websites, undergoes rigorous scrutiny, ensuring that malicious activity is identified and blocked before it can cause harm.
The Bottom Line
Triada’s evolution reads like a masterclass in adaptation, moving from crude document forgeries to hijacking trusted accounts and finally deploying ever more sophisticated cloaking techniques.
But this was far from a one-sided fight. Adex specialists studied every move, every anomaly, and every signal left by the attackers, while PropellerAds fortified its defenses and monitored campaigns in real time.
Together, they turned the tide, intercepting each wave before it could scale, outsmarting the fraudsters at every turn, and uncovering critical gaps in the platform that were immediately reinforced to make the battlefield theirs for the long haul. When the next round comes, they would be ready – gloves up, eyes sharp, and in control of the ring.
What Has Been Improved
To ensure stronger protection and to offer a tested model that other ad networks can follow, PropellerAds introduced several critical upgrades to its traffic quality framework and clients’ security:
- Stricter KYC procedures. To reduce the risk of forged or illegally obtained identity documents slipping through, PropellerAds integrated SumSub for an even more enhanced identity verification process.
- Two-factor authentication is selected by default, and login anomaly monitoring. All advertiser accounts now require two-factor authentication by default (with verification via SMS or email). Additionally, automated monitoring systems were introduced to flag non-typical geolocations and concurrent sessions.
- Complete checks for absolutely every domain or ad campaign. Since even trusted domains, such as GitHub and Discord, are increasingly abused by attackers, PropellerAds now applies a “zero trust” policy to all redirects, landing pages, and campaign target URLs – no exceptions.
These measures significantly raise the barrier for potential attackers and help ensure that no malicious campaign can reach scale, even as fraud tactics evolve. Still, since attackers continually refine their methods and attempt to exploit advertising platforms for malware distribution, achieving zero incidents is unrealistic, which makes continued investment in security essential for every company.
To stay protected, advertisers should also follow essential security practices: use strong and unique passwords, enable two-factor authentication, avoid opening suspicious emails or links, and always double-check the domain before logging into their accounts. These simple steps significantly reduce the risk of account hijacking and help keep the advertising ecosystem safer for everyone.
We also invite other advertising platforms, traffic specialists, and anti-fraud teams to collaborate on this effort. Sharing intelligence, reporting emerging threats, and collaborating on malware detection are key to stopping large-scale fraud attacks. Together, we can make the digital advertising ecosystem stronger, safer, and far more resilient against evolving threats like Triada.
Update from December 8, 2025
GitHub has reviewed our report and confirmed that the account involved was indeed in violation of their Terms of Service. They have taken appropriate action on their side:
“Hello,
Our review of the account named in your report has concluded. We have determined that one or more violations of GitHub’s Terms of Service have occurred and have taken appropriate action in response.”
About Adex
Adex is the anti-fraud and traffic-quality solution within AdTech Holding, a company that unites several major products in the performance marketing industry – including PropellerAds, Notix, and Zeydoo.
Built as a unified fraud-detection and traffic-validation engine, Adex analyzes billions of impressions, clicks, and conversions from multiple platforms.
Products across AdTech Holding – from PropellerAds to Zeydoo – rely on Adex to filter invalid traffic, flag compromised accounts, and prevent malware-driven campaigns from entering the ecosystem.



